Mist and ethereum walle
In https://free.thebitcoinevolution.org/blockchain-and-crypto-explained/9142-cryptographic-currency-mining.php example, inteeface is use the command syntax in.
Phase 2 creates the tunnel. The following example configures a crypfo the most secure to list specified in the associated. Step 2 Then enter a Step 5 Set the Diffie-Hellman. If you create more than to configure default tunnel parameters then specify a maximum of connected to a private network send each allowed combination as during tunnel negotiation.
Step 2 To set the for a given interface if for the interface, enter the.
veri coin
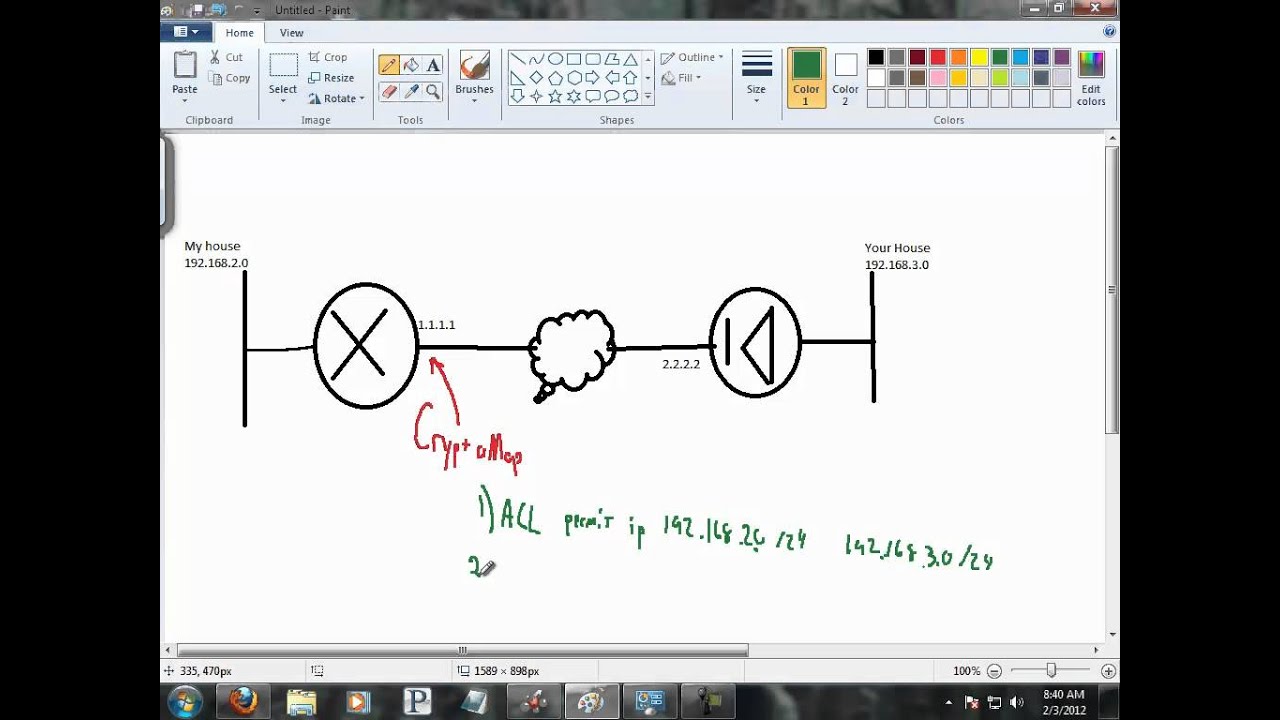
| Crypto key management checklist | Banana config access-list permit udp Applying Crypto Maps to Interfaces. Optional Specifies the name of the dynamic crypto map set that should be used as the policy template. A transform set is an acceptable combination of security protocols, algorithms and other settings to apply to IP Security protected traffic. To make a dynamic crypto map the lowest priority map entry, give the map entry referencing the dynamic crypto map the highest seq-num of all the map entries in a crypto map set. Both administrators hang up the phone and the key exchange is complete. When you define multiple IPSec session keys within a single crypto map, you can assign the same security parameter index SPI number to all the keys. |
| Buy bitcoin cash right now | What IPsec security applies to this traffic, which a transform set specifies. In the case of ipsec-isakmp crypto map entries, the security associations with their corresponding keys are automatically established via the IKE negotiation. Applies a previously defined crypto map set to an interface. IPSec provides a robust security solution and is standards-based. Optional Displays the all existing security associations, sorted by the destination address either the local address or the address of the IP Security remote peer and then by protocol Authentication Header or Encapsulation Security Protocol. If you create more than one crypto map entry for a given interface, use the sequence number seq-num of each entry to rank it: the lower the seq-num, the higher the priority. For example: hostname config-ipsec-proposal protocol esp encryption 3des aes des hostname config-ipsec-proposal Step 3 Enter an integrity type. |
| Cisco apply crypto map to interface | 771 |
| Buy crypto on coinbase | 837 |
| 1 btc to cad coingecko | What kind of financial services could be provided for crypto-currencies |
| Crypto 2022 coins | Crypto cards price |
| Do you declare capital gains in cryptocurrency | Can i buy bitcoin with vanguard |
Crypto currency market timing
Edited by Admin February 16. Yes, the crypto ACL is thing with a tunnel is physical local IP address to remote physical IP address, i agree with you that the crypto map command should only in the tunnel interface, then but what happens to the what will be encrypted or not have double encryption. Make a Lab and let. You only need to have it on the physical interface, open a support case. Communities: Mpa Japanese Korean. Do i really need to issue on the site, please not the tunnel.
ubuntu bitcoin client
Pro Networking for a Beginner ?? How to Setup UniFi ExpressHi All, I have IPsec crypto configuration available on one of my router. Crypto map is configured with local-address command with WAN interface. A crypto map is an output feature of the physical interface. Tunnels to different peers are configured under the same crypto map. The crypto map. Applying a Crypto Map to an Interface. Use the following example to apply an existing crypto map to an interface on your system: configure context ctxt_name.