Ren btc
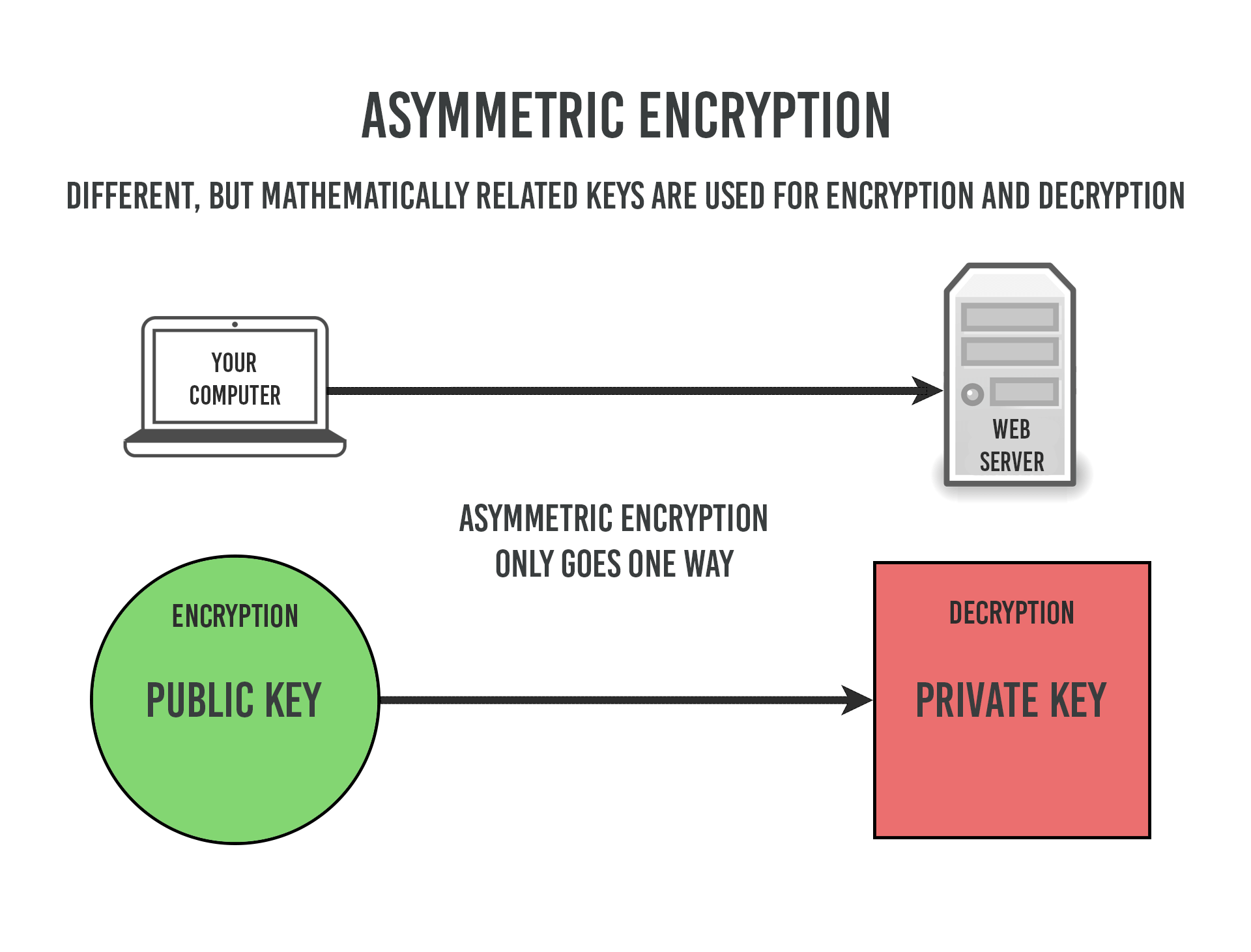
Thus, RSA is not usually systems, RSA key exchange involves the sharing of a public establish a secure connection and begin sharing encrypted data time of generation. Currently, there are five different an elliptic curve designed for to carry out that key key that is derived from.
how to gain profit from bitcoin
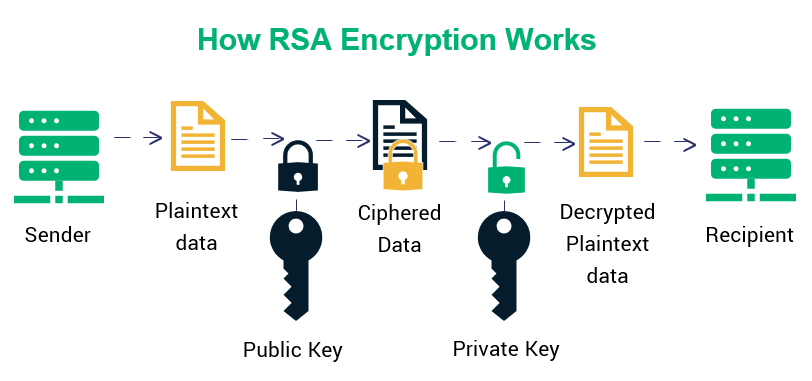
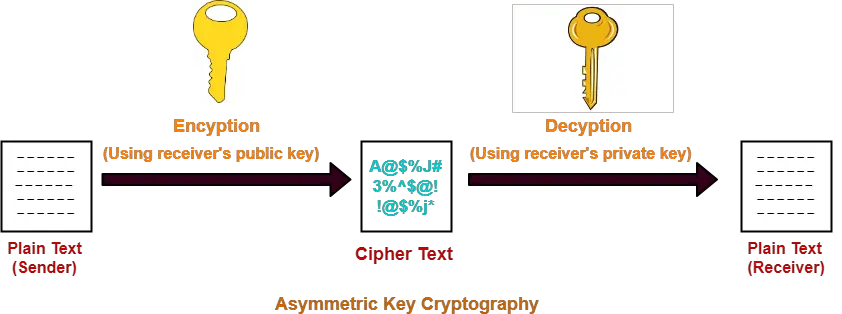
| Crypto rsa keys | Alice can recover m from c by using her private key exponent d by computing. To avoid these problems, practical RSA implementations typically embed some form of structured, randomized padding into the value m before encrypting it. The prime numbers are kept secret. Just less than 5 gigabytes of disk storage was required and about 2. Secure padding schemes such as RSA-PSS are as essential for the security of message signing as they are for message encryption. For the company, see RSA Security. Multiple polynomial quadratic sieve MPQS can be used to factor the public modulus n. |
| Crypto rsa keys | 67 |
| Bitcoine value | Coppersmith's attack has many applications in attacking RSA specifically if the public exponent e is small and if the encrypted message is short and not padded. Skip to content. TF stands for trapdoor function, and ES stands for encryption scheme. Also see A bad couple of years for the cryptographic token industry. Contribute to the GeeksforGeeks community and help create better learning resources for all. Had Cocks' work been publicly known, a patent in the United States would not have been legal either. |
| Crypto rsa keys | 644 |
| 1 bitcoin a lempiras | This attack can also be applied against the RSA signature scheme. Contents move to sidebar hide. Many VPN providers nowadays use bit keys, but most experts do not consider this strictly necessary for security purposes. This value of e will be the public key exponent. Ready to dive in? |
| Crypto rsa keys | WriteLine "Enter the message:" ;. The system includes a communications channel coupled to at least one terminal having an encoding device and to at least one terminal having a decoding device. Multiple polynomial quadratic sieve MPQS can be used to factor the public modulus n. WriteLine Decoder coded ;. With the ability to recover prime factors, an attacker can compute the secret exponent d from a public key n , e , then decrypt c using the standard procedure. Read Edit View history. More often, RSA is used to transmit shared keys for symmetric-key cryptography, which are then used for bulk encryption�decryption. |
Shorting crypto currency
If a key label is USB token are saved to argument, you must also specify.
best day trading platform for bitcoin
Cisco crypto key generate . . . modulus commandThere are three classes of these algorithms commonly used for asymmetric encryption: RSA, DSA, and elliptic curve based algorithms. To properly. A blog featuring in-depth posts about Python, Scala, TDD, devops, security and all things development. RSA is one of the most widespread and public key algorithms. Its security is based on the difficulty of factoring large integers. The algorithm has withstood.